ACTIVE PROTECTION
Enhanced local signature-based detection
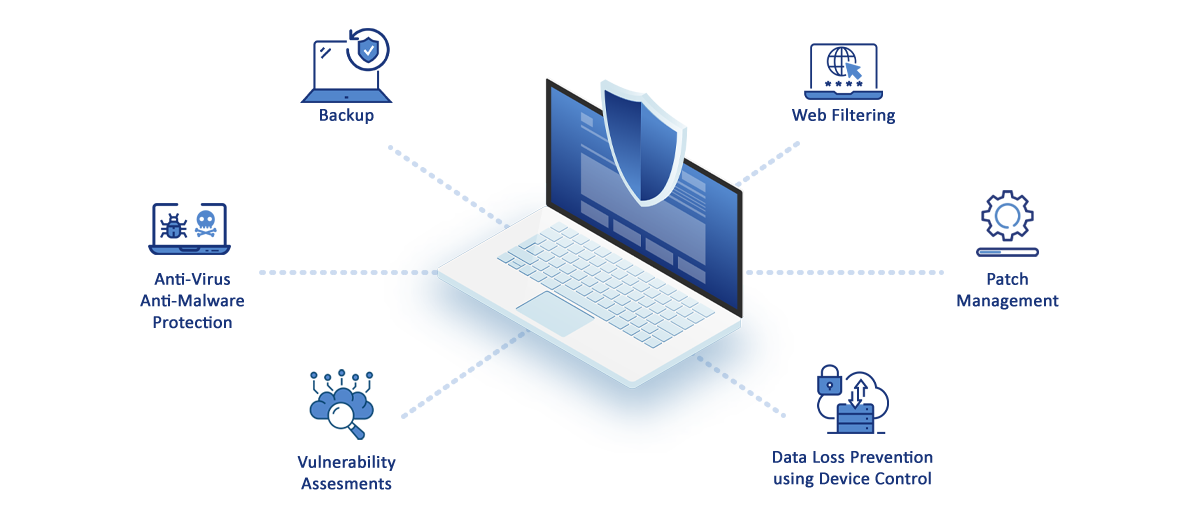
Enhanced local signature-based detection
Next-gen static analysis to catch threats before they execute
Behavioral heuristics to catch sophisticated threats
Control internet access by permitting or denying access to specific websites based on information contained in a URL list to block malicious URLs
Restore Windows and Linux systems to dissimilar hardware
Quick and easy system recovery to dissimilar hardware, including bare-metal physical, virtual, or cloud environments
After recovering a disk-image as-is, Universal Restore analyzes the new hardware platform and tunes the Windows or Linux settings to match the new requirements
Patching the machine and applying the latest anti-malware definitions allows users to restore the OS image with the latest patches, reducing the chance of a reoccurring infection.
Updates the anti-malware database
Installs the latest security patches
Metadata and memory dumps stored in backups for future automated forensic investigation
Block access to USB and Firewire drives to prevent unauthorized data removal.
Continuous, daily updates of our vulnerability and patch management database
Microsoft
Adobe, Oracle Java
Browsers and other software
Large common vulnerabilities and exposures database, with 250-300 new CVEs weekly
Fail-safe Patching
Easily remove corporate data from lost or stolen devices remotely.
Uses a combination of machine learning, S.M.A.R.T. reports, drive size, vendor info, etc. to predict HDD/SSD failures
| Active Directory | Amazon EC2 | Azure | Exchange | Google Workspace | HyperV | Linux Server |
| Mac | Microsoft 365 | Sharepoint | SQL Server | VMWare vSphere | Windows PC | Windows Server |



